
If we’ve heard it once, we’ve heard it dozens of times. There are countless aspects to consider in cybersecurity, and as technology continues to advance at a rapid pace, so do the risks associated with our digital infrastructure. In this blog, we’ll navigate the landscape of cybersecurity vulnerabilities, threats, and risks that can impact businesses of all sizes.
But before we go any further, let’s make sure we completely understand these three key principles of security: vulnerabilities, threats, and risk.
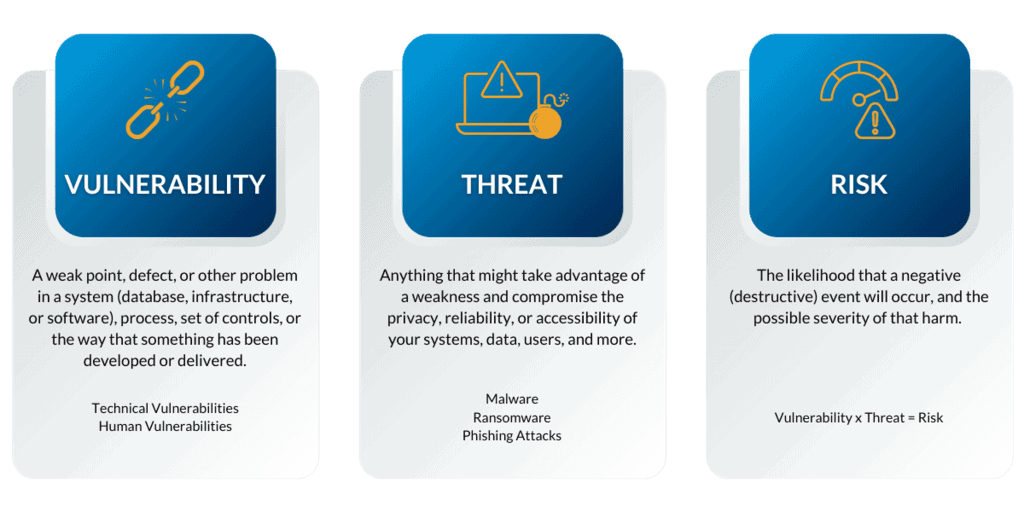
Cybersecurity Vulnerabilities Vs. Threats Vs. Risks
Although these words are commonly used interchangeably, they really refer to three different cybersecurity components. In a nutshell, they may be viewed as a spectrum:
- For starters, a vulnerability subjects your business to attacks.
- A threat is a hostile or harmful occurrence that exploits a vulnerability.
- Finally, a risk is the possibility of loss and damage if the threat occurs.
Let’s take a closer look at each of these.
What Are Cybersecurity Vulnerabilities?
A cybersecurity vulnerability is a weak point, defect, or other problem in a system (database, infrastructure, or software), but it can also occur in a process, a set of controls, or even just the way that something has been developed or delivered.
There are several vulnerabilities, which can be broadly categorized as follows:
Technical Vulnerabilities – such as software flaws or hardware/software errors:
IoT: These are everyday items that are networked and incorporated with software. IoT device vulnerabilities can arise from old software, inadequate default configurations, or poor security procedures used during development. Smart refrigerators, wearables, and thermostats are a few examples.
Devices (computers, mobile phones, and tablets): These endpoints are where the majority of user interactions take place, and these devices can have software vulnerabilities due to out-of-date operating systems, unpatched software, or unsafe applications. Examples include iPads, Android/iPhone, Windows PCs, etc.
Human Vulnerabilities – such as workers falling victim to phishing, smishing, or other typical assaults (learn more about this here):
Instead of software flaws, social engineering or insider threats can take advantage of human weaknesses. It’s particularly harmful because it relies on human error rather than operating system or software flaws. Examples include using psychological tricks to persuade users to make security mistakes or divulge critical information.
Some vulnerabilities are expected; you just release something and then soon issue a patch to fix it. The problem arises when your team is unaware of or unable to identify the vulnerability. If left unchecked, it can easily be exposed to an attack.
A vulnerability can be compared to leaving your door unlocked while you sleep. It’s not an issue by itself, but if a specific individual enters that door, you can easily find yourself in a bad situation – and the more vulnerabilities you have, the larger the possibility for attacks and the higher your risk.
What Are Cybersecurity Threats?
The most typical description of a threat in cybersecurity is anything that might take advantage of a weakness and compromise the privacy, reliability, or accessibility of your systems, data, users, and more.
Malware, ransomware, phishing assaults, and other dangers are some examples of this, and new threats are always emerging and evolving. However, not all threats are created equal – this is where threat intelligence comes into play. An attacker may be willing and able to cause harm, but they lack the means and opportunity to do so.
For instance, a good patch management program or effective network segmentation policies that restrict access to crucial systems may mean that your firm has no vulnerabilities that could be exploited. However, there’s a good chance that you do have vulnerabilities, so let’s think about the risk element.
What Are Cybersecurity Risks?
Risk is both the likelihood that a negative and/or destructive event will occur, and the possible severity of that harm. Due to a combination of internal and external factors, your organizational risk changes over time, sometimes occurring on a daily basis.
It sounds challenging at first, until we simplify it. Something is always at risk – whether it’s a system, equipment, business processes, bank account, the reputation of your company… you get the idea. The good news is that there is a way to try and measure that risk:
- Estimate the likelihood of an attacker attempting to exploit a vulnerability and produce the targeted harm.
- Analyze the resilience of your current systems, controls, and procedures in the face of these challenges.
- Calculate the potential effect or harm that the attacker could cause if they succeed.
One approach to describe risk was consequence X likelihood, but as security teams’ methods and intelligence have progressed, we’ve discovered that you must also account for the safety measures you’ve already put in place.
This is another, rather simplified, method of looking at risk:
Vulnerability x Threat = Risk
We can summarize this calculation using the ideas from above: you can get an estimate of the risk involved by multiplying a single vulnerability by the possible threat (frequency, current protections, and potential value loss). Organizations must first identify their vulnerabilities and the threats to those vulnerabilities before they can begin risk management and mitigation.
What Can You Do?
This fundamental truth—that no matter how sophisticated your systems are, you can’t entirely eliminate or provide protection against all types of threats—is one of the issues with risk. This is where the concept of risk management steps in: a regular, continuous procedure where the appropriate staff periodically reviews risks in order to reduce the likelihood that certain threats could materialize. This includes secure coding procedures, frequent software upgrades and patches, security audits and penetration tests, and security awareness training for employees.
Understanding the cybersecurity vulnerabilities, threats, and risks that your business is prone to will allow you to make strategic decisions that not only protect your data, but also your employees, IT infrastructure, and business as a whole.
If you’re interested in learning more about cybersecurity vulnerabilities, calculating your business’s risk, or risk management strategies please contact us and call (502) 240-0404 or email info@mirazon.com.