If you’re trying to track down who sent out those company secrets or correspondence regarding a legal issue, you can use the Office 365 Security and Compliance features.
First, Set Up Proper eDiscovery Permissions
Open Office 365 using Microsoft Edge. Log on as an administrator and open the “Security and Compliance” console:
 or
or ![]()
Permissions should only be granted to the level needed to perform the task at hand. For a deeper explanation of Compliance permissions, check out this Microsoft article.
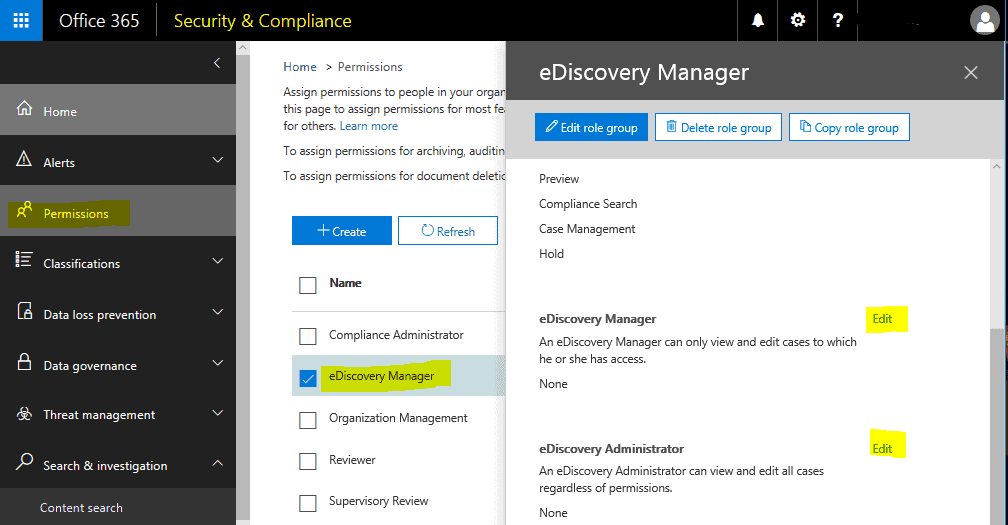
For this particular case we will be assigning the “eDiscovery Manager” permissions.
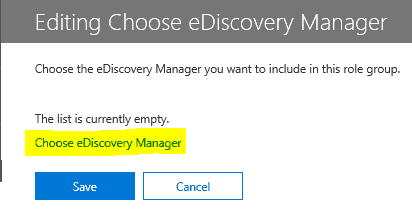
Select “Permissions”, “eDiscovery Manager” and edit the eDiscovery Manager to add the account which will be doing the eDiscovery:
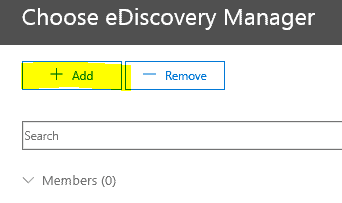
Select “Choose eDiscovery Manager”:
Select Add:
After assigning that user the eDiscovery permissions, give Office 365 time to propagate those changes. This usually takes less than 15 minutes. If you are using that account I would recommend logging off while it propagates.
Create a Content Search
Drill down to “Search and Investigations” and “Content search”, as shown below:
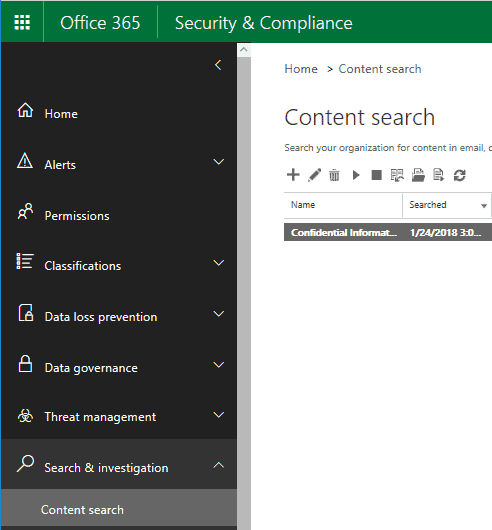
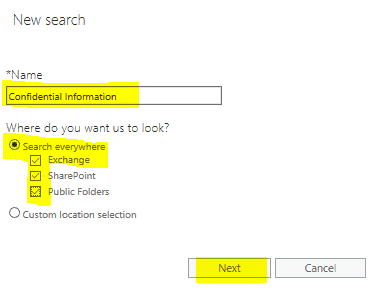
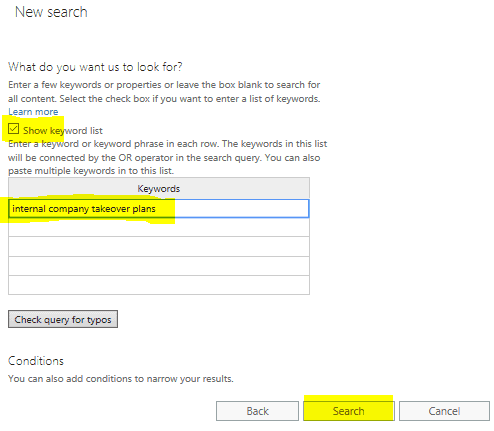
Once you click “Search” it will begin immediately searching your “indexed” database.
Note: Indexed means email and data it can scan and index. It may skip attachments or larger email threads. Soft deleted items are also indexed.
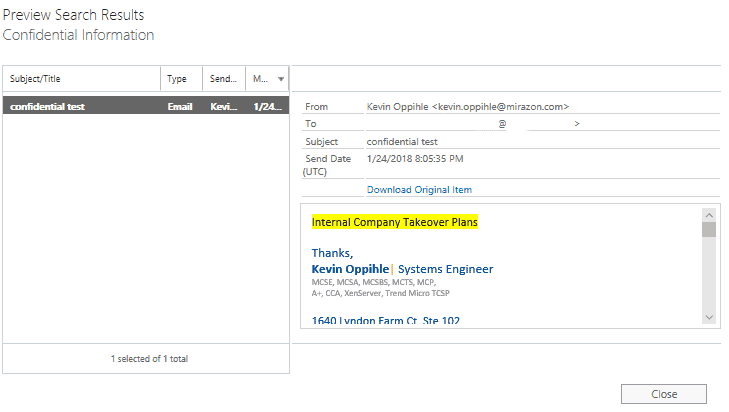
To the right you will see the search results. As you can see below my search grabbed the one email regarding “internal company takeover plans”. To view what specific emails it found you can “preview search results”:
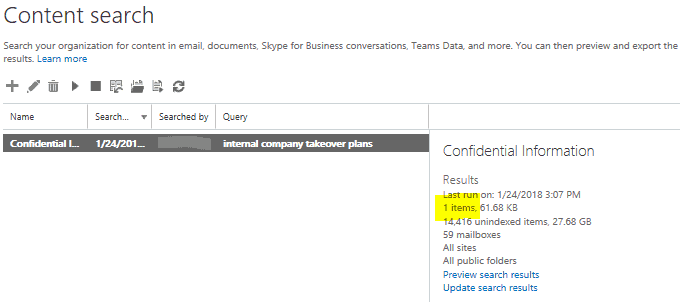
Opening the Preview Search Results:
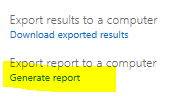
If you would like to export the results to a CSV file, go to “Export report to a computer” and click on “Generate report” underneath it, as shown below:
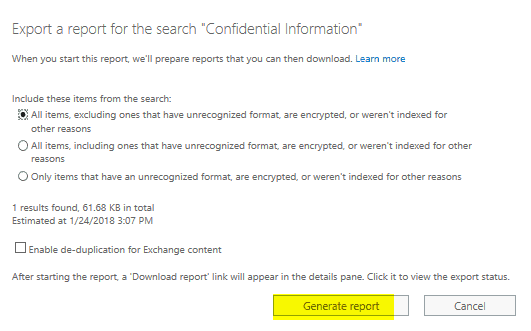
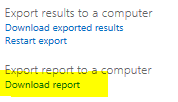
If you need to export all the emails to PST under “Export results to a Computer” click “Start Export” as shown below:
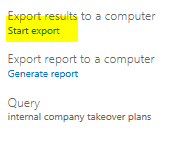
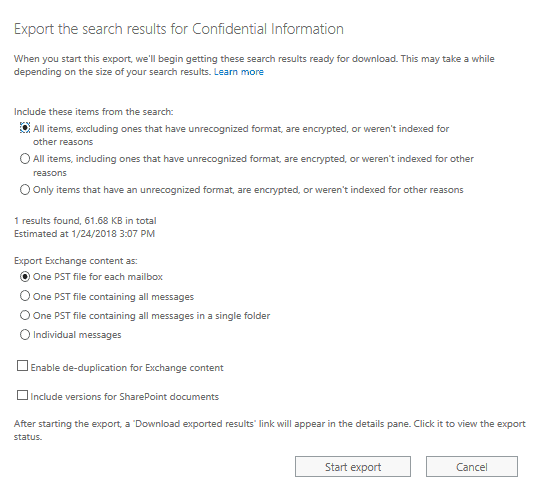
Transferring the Data into OnsiteReport or PST:
Whether you download PSTs or the report, you will receive an export key as shown below. Copy it and then click on “download results”:
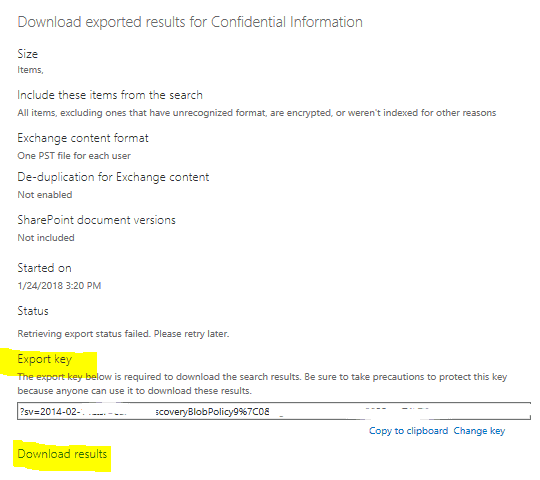

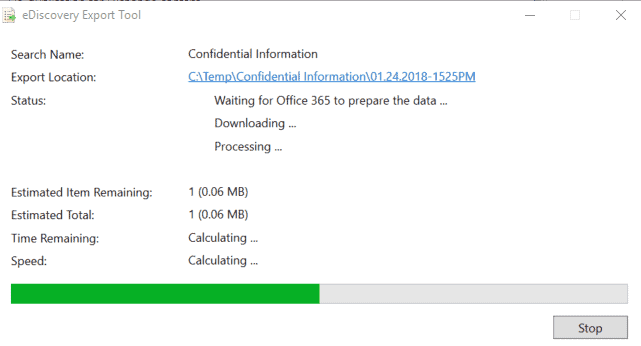
Note: Soft deleted emails will be listed and exportable by the query till they are hard deleted from the mailboxes.
Note: This can also be used to delete small batches of emails such as companywide phishing email blasts.