Reach Out – We're Listening!
Have questions or need assistance? Drop us a line – we can’t wait to meet you.
Headquartered in Louisville, Kentucky, we proudly deliver world-class IT support and solutions to customers across the nation.
Cybersecurity Services
Information security has never been more critical to organizations of all sizes. Bad actors are constantly attacking networks, preying on unsuspecting end users, and/or trying to infect your systems with ransomware.
Through years of experience in configuring network security systems and remediating nasty malware attacks, Mirazon has honed a robust strategy for both preventing and mitigating cybersecurity breaches.
With our different security assessment packages, we can help you see what you’re doing right and new areas to improve.
End users must recognize bad actors’ attempts to infiltrate your network through spam, phishing, smishing, spear phishing, quishing, and other ever-evolving social engineering strategies.
Our experts stand as your vigilant guardians in the realm of cybersecurity. In a world where threats constantly evolve, we ensure that your digital landscape remains secure, resilient, and ahead of potential attackers.
Preventing or suffering from a ransomware attack is hard – we understand how stressful and overwhelming it can be. Mirazon can help – however you need us.
Your business’s data is crucial to your operations, but is also a large attack vector and risk. Securing and safeguarding your data from hacking or loss is a moving target – and we have perfect aim.
Let the experts set up, monitor, and maintain your network. We use up-to-date best practices to keep you secured and functioning.
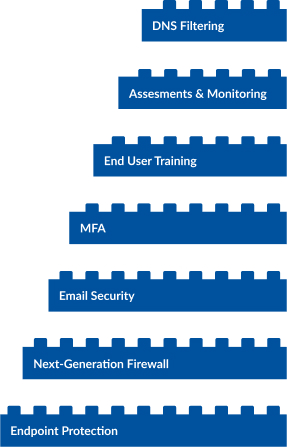
Cybersecurity threats are ever-evolving. The only way to combat this is with the mindset of assuming it’s a case of when and not if – how do you limit the scale of an attack?
With Mirazon’s Layered Security Strategy, you will be able to identify, stop, and minimize cyberattacks.