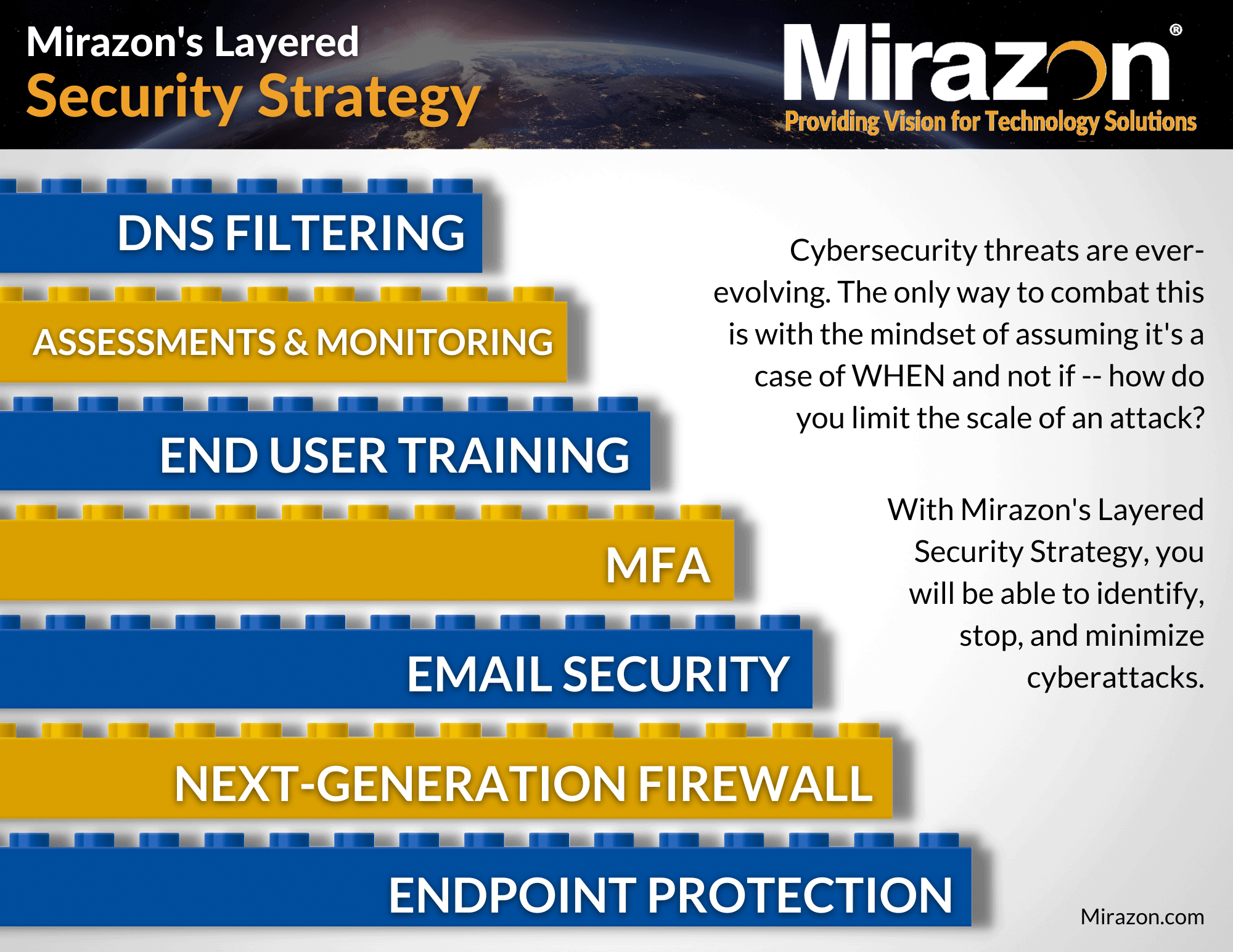
Our previous Defense In Depth blog covered next-generation firewalls (NGFW). The next layer in our Layered Security Strategy is all about email security and how it plays a vital role in your business’s overall defense in depth strategy.
In today’s world, enterprises heavily lean on email for communication and data transfer. Employees collaborate, save information, and clients make requests via email. Email is what makes us money. Nevertheless, this is accompanied by a significant concern regarding data privacy and security breaches.
Email security is now at the top of the priority list of IT departments due to the escalating cyber threats – such as phishing attacks, malware attacks, and the ever-evolving social engineering tactics – it’s imperative for businesses to adopt a proactive stance in staying ahead of these potential risks. Email is not only an absolutely mission-critical piece of business technology, but it is one of the more vulnerable attack surfaces due to direct access to the end user.
In this blog post, we will discuss different elements within email security, their importance, and how they contribute to maintaining a secure IT environment.
Download Our Layered Security Strategy Whitepaper
Elements Of Email Security
Proper email security should act like the floodlights to your home – catching bad actors before they have a chance to breach the systems. It’s a crucial aspect of ensuring the confidentiality, integrity, and availability of emails and the information they contain.
Email security involves implementing various measures and protocols to protect against unauthorized access, interception, and manipulation of email communications. By employing encryption, spam filtering, anti-malware techniques, multi-factor authentication (MFA), security awareness training (SAT), and data loss prevention (DLP), you’re better able to safeguard sensitive data from being compromised.
Check Out Our Exchange Security Unveiled Blogs
So, let’s dig into these elements…
Encryption
Encryption is the process of converting data into an unreadable format to protect it from unauthorized access – similar to turning a message into a secret code so that only the intended receiver can understand it. The key characteristic of this transformation is that only those with the correct key, usually the intended recipient, possess the means to decrypt and convert it back to its original, understandable form.
Within the realm of email security, one of the most powerful tools leveraging encryption is end-to-end encryption, which encrypts the email at the sender’s device and only decrypts at the recipient end. This ensures that even during transit, the email remains a cryptic message to any prying third-party eyes. It’s like sending a secret letter that only the intended receiver has the special decoder for.
Encryption serves as a robust safeguard, preventing unauthorized individuals, hackers, or malicious entities from deciphering the contents of the email, even if they manage to intercept it during its journey.
In essence, encryption in email security operates as a guardian, preserving the integrity and confidentiality of the email’s contents. Its role is fundamental in upholding trust and confidence in the digital communication landscape, where privacy and data security are paramount concerns.
Spam Filtering
Spam emails are a common method that attackers use to spread a variety of cyber threats, including malware, phishing links, and deceptive scams. These unsolicited emails flood inboxes worldwide, often masquerading as legitimate communications, aiming to deceive recipients and trick them into taking detrimental actions.
To counter this threat, spam filtering is a crucial preventive measure, acting as the gatekeeper against the overflow of spam emails.It intercepts and impedes these malicious emails from infiltrating the organizational network and, ultimately, reaching the end users.
These specialized filters are finely tuned to detect subtle markers of malicious intent within spam emails. They scrutinize elements like sender information, email structure, embedded links, and attachments to differentiate between legitimate emails and potentially harmful ones. Upon detection of spam, these filters take swift action, diverting suspect emails away from users’ inboxes and quarantining them for further analysis.
Moreover, email security solutions, such as Proofpoint, bolster this defense mechanism by serving an additional function: email gateway security. Their primary objective is to deny entry to any suspicious or harmful content, particularly spam emails or emails coming from compromised senders. By proactively identifying and intercepting spam or email sent from known not-good sending addresses at the network perimeter, they effectively mitigate the risks posed by these malicious messages even more than typical spam filtering products/services.
In essence, this combined effort of spam filtering and email gateway security solutions significantly elevates the overall resilience of an organization’s email security infrastructure. It not only helps prevent the flood of malicious spam, but also plays a crucial role in averting the potential damage that can result from the harmful payloads often concealed within these emails.
Antivirus/Anti-Malware
When antivirus fails you, having endpoint protection is key.
Malware attacks represent a persistent threat in the digital landscape, capable of infiltrating a user’s devices and wreaking havoc by stealing sensitive data or compromising system functionalities. Malware can manifest in various forms, such as viruses, worms, trojans, ransomware, spyware, and adware – each with its own destructive agenda.
To fortify the defenses of digital devices and networks against these threats, the deployment of antivirus software is critical. This software acts as a watchman, continuously monitoring the device for any signs of malicious software. It functions by detecting and neutralizing malware, preventing it from executing code and causing harm to the system.
One of the key roles of antivirus software is to scrutinize attachments and links associated with emails, downloads, or websites. It’s important to understand that antivirus software extends its protective shield beyond your device, especially when it comes to email security. When you receive an email, the antivirus component of your security software scans the attachments and links included in the email. This is where the magic happens.
Prior to opening these potentially hazardous elements, the software performs thorough scans to identify any traces of malicious code. It checks for viruses, Trojans, or any other forms of malware that might be hiding within those attachments or links. It functions proactively to ensure that you’re not exposed to harmful content, and if it detects any malicious elements, it notifies you. This notification is a crucial defense mechanism, allowing you to steer clear of the dangerous content and take the necessary precautions.
However, antivirus does have the potential to fail you…
Now, considering the ever-evolving landscape of cybersecurity, it’s important to acknowledge that relying solely on traditional antivirus might not be sufficient. Cyberthreats are constantly devising sophisticated techniques to bypass security measures. This is where the question of whether you should focus on Endpoint Detection and Response (EDR) instead of or in addition to traditional AV comes into play.
While traditional antivirus software plays a vital role in preventing known malware from entering your system, EDR solutions offer a more advanced layer of protection. EDR goes beyond signature-based detection, relying on behavioral analysis to identify and respond to new and unknown threats. It offers a more comprehensive approach to cybersecurity, making it imperative to implement a multi-layered security strategy.
In this ever-changing threat landscape, we recommend considering a Layered Security Strategy that combines both traditional antivirus and EDR solutions. This approach enhances the overall protection of your IT infrastructure, ensuring that you’re well-prepared to defend against any threats that may come your way.
Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is like having multiple locks on the door to your accounts, making it much harder for anyone to break in. It’s a security setup that requires you to provide not just one, but at least two or more types of information to prove you’re the rightful account owner. MFA consists of three elements: something the user knows, something the user has, or something the user is.
The first element of MFA is “something the user knows,” like a secret PIN, a password, or answers to specific security questions. It’s your way of showing what you’ve memorized and kept private.
The second element is “something the user has,” such as a physical security token, a mobile app that generates one-time codes, or a smart card. It’s a tangible item you possess and can use to verify your identity.
The third element, “something the user is,” involves biometrics—unique physical or behavioral characteristics like a fingerprint, facial recognition, or voice patterns. This element uses your distinct biological traits to confirm your identity.
By combining two or more of these elements, MFA ensures that only authorized users can access their email accounts. Even if someone figures out your password, they would still need that extra piece of information—a fingerprint scan, for instance—to get in. It’s like having a secret handshake that only you know and possess, making your email account and, therefore, your business and IT infrastructure, a lot safer.
Why is this incredibly important for your email? Well, we’ve seen several instances where a user’s email was compromised and the bad actor was masquerading as them, requesting wire transfers or sensitive documentation from unsuspecting team members.
Security Awareness Training (SAT)
Security Awareness Training (SAT) stands as a crucial pillar in the realm of, not only your email security, but your business’s security. Recognizing that humans often represent the weakest link in the security chain, educating employees about email security best practices becomes paramount. It’s akin to equipping them with the knowledge and tools needed to be the first line of defense against potential cyber threats.
In these training sessions, powered by Proofpoint, employees are guided on how to recognize suspicious emails. They learn to scrutinize email addresses, look for telltale signs of phishing attempts, and identify grammatical or formatting inconsistencies that may indicate malicious intent.
Understanding the red flags empowers employees to exercise caution and alertness when interacting with their email inboxes. It cultivates a culture of vigilance, enabling the workforce to play an active role in fortifying the organization’s email security infrastructure, and thus, the business as a whole.
Learn More About Security Awareness Training
Data Loss Prevention (DLP)
Another vital aspect of email security, integral to a comprehensive layered security strategy, is Data Loss Prevention (DLP). DLP acts as a vigilant guard on duty, scanning the contents of outgoing emails to ensure that sensitive information like credit card numbers, social security numbers, or bank routing details isn’t being inadvertently shared or leaked.
In essence, DLP is a function integrated within your email security infrastructure or, sometimes, within your firewall. It’s designed to recognize patterns or formats that match sensitive data, like credit card numbers or social security numbers. If such patterns are detected, the DLP system triggers and halts the email from being sent, preventing potential data breaches or unauthorized distribution of critical information.
For instance, if an employee inadvertently attempts to send an email containing credit card information, the DLP system will detect this and intervene, either blocking the email or notifying the sender to ensure they are sending it securely and to the appropriate recipient.
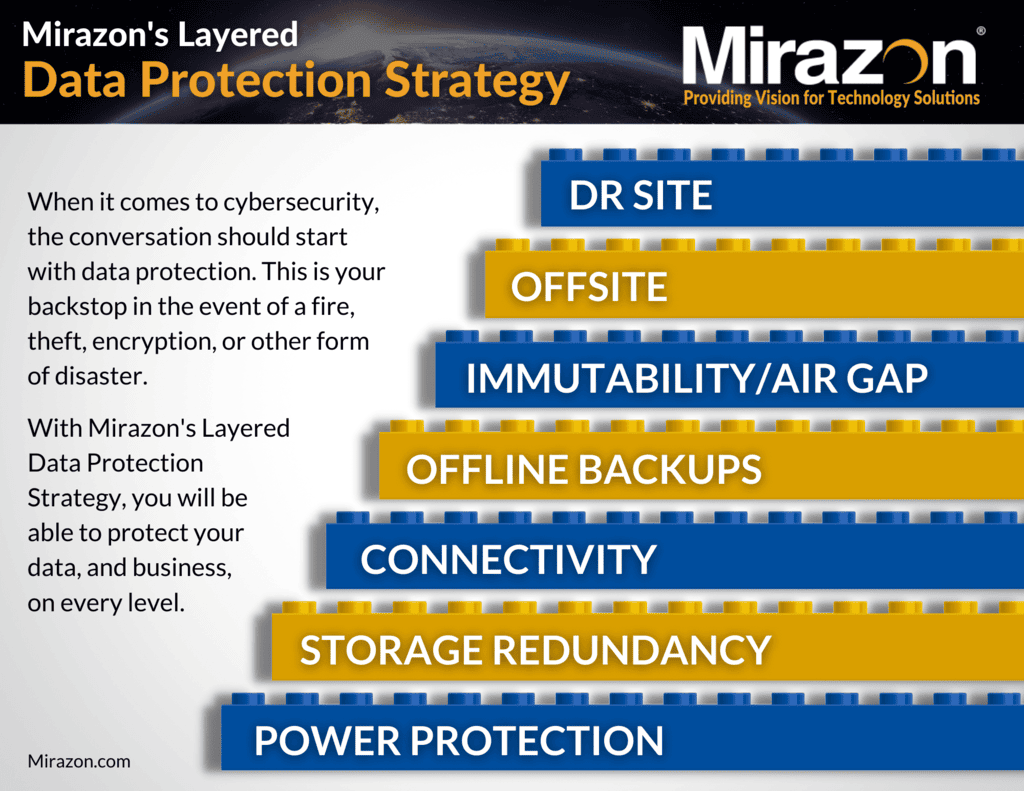
Download Our Layered Data Protection Strategy Whitepaper
Integrating DLP into your email security measures significantly strengthens your defense against data breaches and ensures compliance with regulatory requirements regarding the protection of sensitive information. It complements the above elements, and is a proactive step towards mitigating the risks associated with inadvertent data leaks – which can have severe consequences for your organization.
Conclusion
Email security is a critical component of maintaining a secure IT environment. However, you should go beyond only using the tools included with your email provider, and implement additional security software, such as Proofpoint, to stay ahead of the ever-evolving threats plaguing today’s digital world.
No single method can guarantee 100% protection from cyber-attacks, which is why a multi-layered approach is recommended. By implementing encryption, spam filtering, anti-malware/antivirus, MFA, SAT, and DLP, businesses can protect sensitive information and secure their digital assets.
It’s equally important for IT managers to collaborate across departments and devise comprehensive strategies to safeguard their businesses from cyber-attacks. Don’t wait until it’s too late – take action to protect your business from cyber threats now.
Stay tuned for our next Defense In Depth blog!
If you’d like to learn more about email security and how you can use it to better protect your business, please contact us by calling (502) 240-0404 or emailing info@mirazon.com.