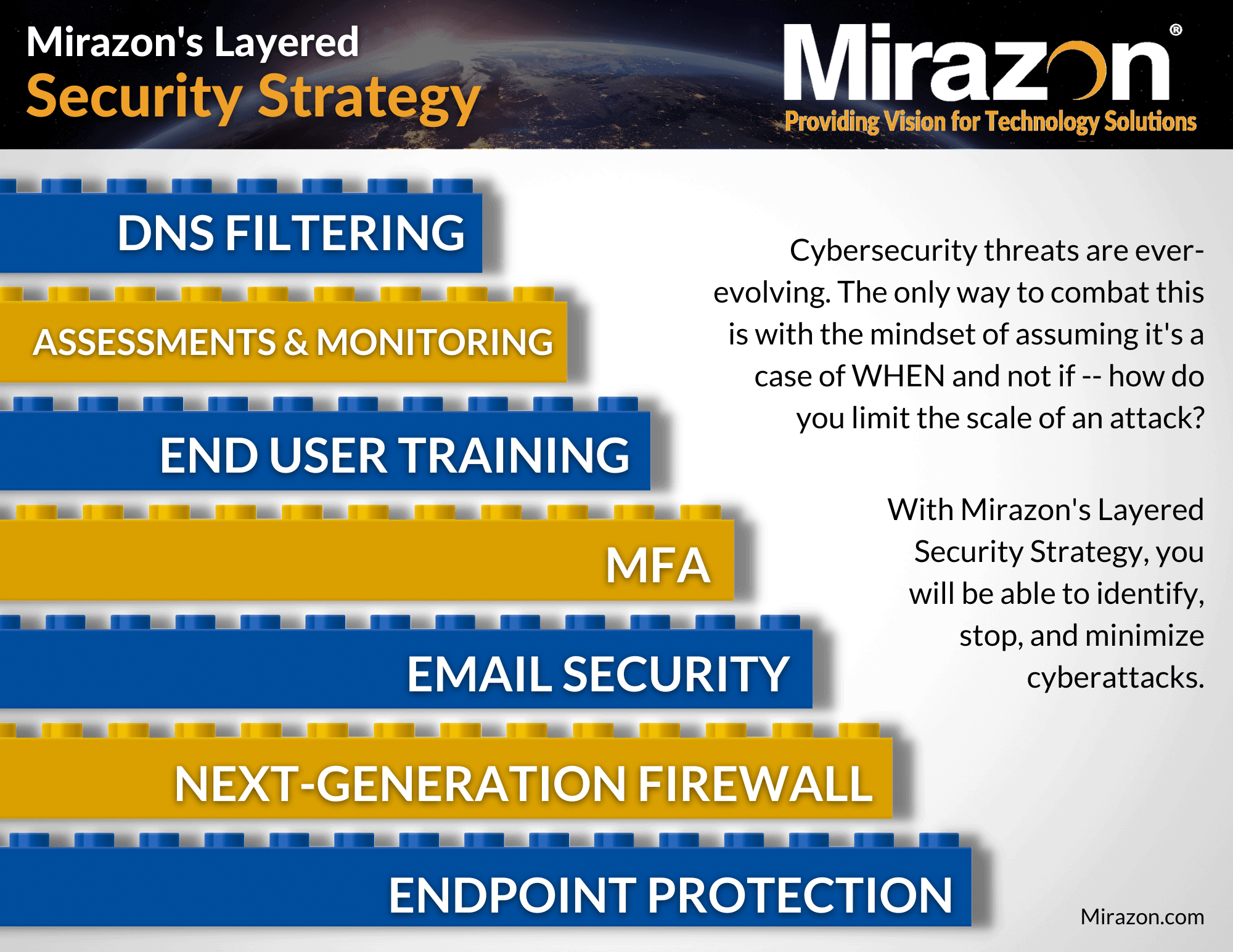
So far, we’ve talked about the first five layers of our Layered Security Strategy. From endpoint protection and Next-Generation firewalls (NGFWs), to email security, MFA, and end-user training, you’d think we’ve covered it all. However, there are two more crucial layers, and in this blog post we will be focusing on IT assessments and monitoring, discussing what they are, the different types and elements involved, and why they’re essential to having a robust layered security strategy.
What Are IT Assessments?
IT assessments are a process of evaluating the security status of an organization’s IT infrastructure, including hardware, software, networks, data storage, and more. They’re designed to pinpoint security gaps, vulnerabilities, and threats – helping to identify weaknesses and potential risks that could be exploited by cybercriminals. Implementing a routine schedule of assessments will not only allow you to measure progress, but it will also help you make smarter technology decisions with the in-depth intelligence they provide.
Elements of IT Assessments
Assess
Keep an eye on internal and external security vulnerabilities, threats, and out-of-date policies that could compromise your security.
Analyze
Determine where you should focus your budget. Establish a baseline for your environment and track your progress as you improve.
Adapt
Sit down with experts to analyze the data and develop actionable, concrete remediation and improvement strategies.
Repeat
Through assessing, analyzing, and adapting, you can repeat successful functions that meet your business’s goals.
Types of IT Assessments
Backups
— Backup Security Assessment
— Outbound Security Report
— Security Management Plan
— Security Policy Assessment
— Security Risk Report
Active Directory
— Anomalous Logins
— Login Failures by Computer
— Security Policies
— User Behavior Analysis
— Windows Patch Assurance
— Security Report Card
— Risk Report
— Management Plan
Office 365
— Azure AD Assessment
— Configuration Change Report
— Management Plan
— Microsoft Cloud Security Assessment
— Microsoft Teams Assessment
— OneDrive Usage
— Outlook Mail Activity Report
— Risk Report
Firewall
— Firewall Security Assessment
— External Vulnerability Scan Detail Report
— External Vulnerability Scan Detail by Issue Report
— External Network Vulnerabilities Summary Report
— External Vulnerability Scan Detail Excel
— Security Risk Report
— Security Management Plan
— Outbound Security Report
General Health
— Windows Patch Assurance Report
— Outbound Security Report
— Security Policy Assessment
— External Vulnerability Scan Detail by Issue
— External Network Vulnerabilities Summary Report
— Login Failures by Computer Report
— User Behavior Analysis Report
— Anomalous Login Report
— Security Report Card
— Management Report
— Risk Report
What Is IT Monitoring?
IT monitoring is the process of observing and analyzing an organization’s IT infrastructure to ensure that everything is functioning correctly. IT monitoring involves tracking the performance of networks, hardware, and software – capturing and analyzing data. Think of it like Swiss cheese — each slice has holes, but if you layer up enough slices, you won’t be able to see through it anymore.
This can be an overwhelming task for SMBs lacking resources, such as time, money, employees, or all of the above. Many SMBs decide to outsource this task to a managed threat detection and response team, like Mirazon, which makes use of the latest innovative technologies (such as CrowdStrike) to defend their infrastructure. Having a managed detection and response team is just one critical slice in your Swiss cheese stack, where our experts stand as your vigilant guardians in the realm of cybersecurity.
The goal of IT monitoring is to detect issues and fix them before they cause any damage. In a world where threats constantly evolve, our experts will ensure that your digital landscape remains secure, resilient, and ahead of potential attackers.
Elements of IT Monitoring
Vulnerability Scans
Vulnerability scans, such as an internal network scan, identify security gaps that could be exploited by anyone with malicious intent.
Pen Testing
Pen testing involves simulating cyber-attacks to check the resilience and strength of an organization’s IT infrastructure to prevent specific types of attacks.
Log Analysis & Reporting
Log analysis tracks and analyzes logs generated by hardware and software, helping detect unusual activities or patterns.
Breach Detection & Alerts
Intrusion detection involves monitoring IT infrastructure for any anomalous behavior or network traffic generated by unauthorized users.
Continuous Security Improvement
As the digital world evolves, so should your security measures, with the aim of sustaining optimal defense and security posture.
Why Are IT Assessments And Monitoring Important?
IT assessments and monitoring are critically important for any organization that processes sensitive data or information. These elements help organizations identify potential vulnerabilities and threats, develop security policies, ensure compliance with best practices and regulations, and reduce the risk of data breaches. Through the monitoring of IT infrastructure, organizations can detect and prevent cyber attacks before they occur.
What Are The Benefits Of IT Assessments And Monitoring?
There are numerous benefits to IT assessments and monitoring. Not only do they help organizations identify security gaps/vulnerabilities and minimize damage inflicted by cyber attacks, but they also cut repair costs and keep track of how the IT infrastructure is performing, alerting you of any abnormal behavior so you can stay ahead of threats. IT assessments and monitoring also help businesses maintain regulatory compliance, build customer trust and loyalty, and demonstrate a robust security posture.
As cyber-attacks continue to evolve, IT assessments and monitoring are increasingly becoming critical to protecting businesses and their customers. By using these tools, you can give your organization the competitive advantage it’s been looking for and deserves.
Stay tuned for our last Defense In Depth blog, which will cover the importance of DNS filtering and how it contributes to the overall security of your IT infrastructure.
If you’re interested in learning more about IT assessments and monitoring, please contact us by calling (502) 240-0404 or emailing info@mirazon.com.