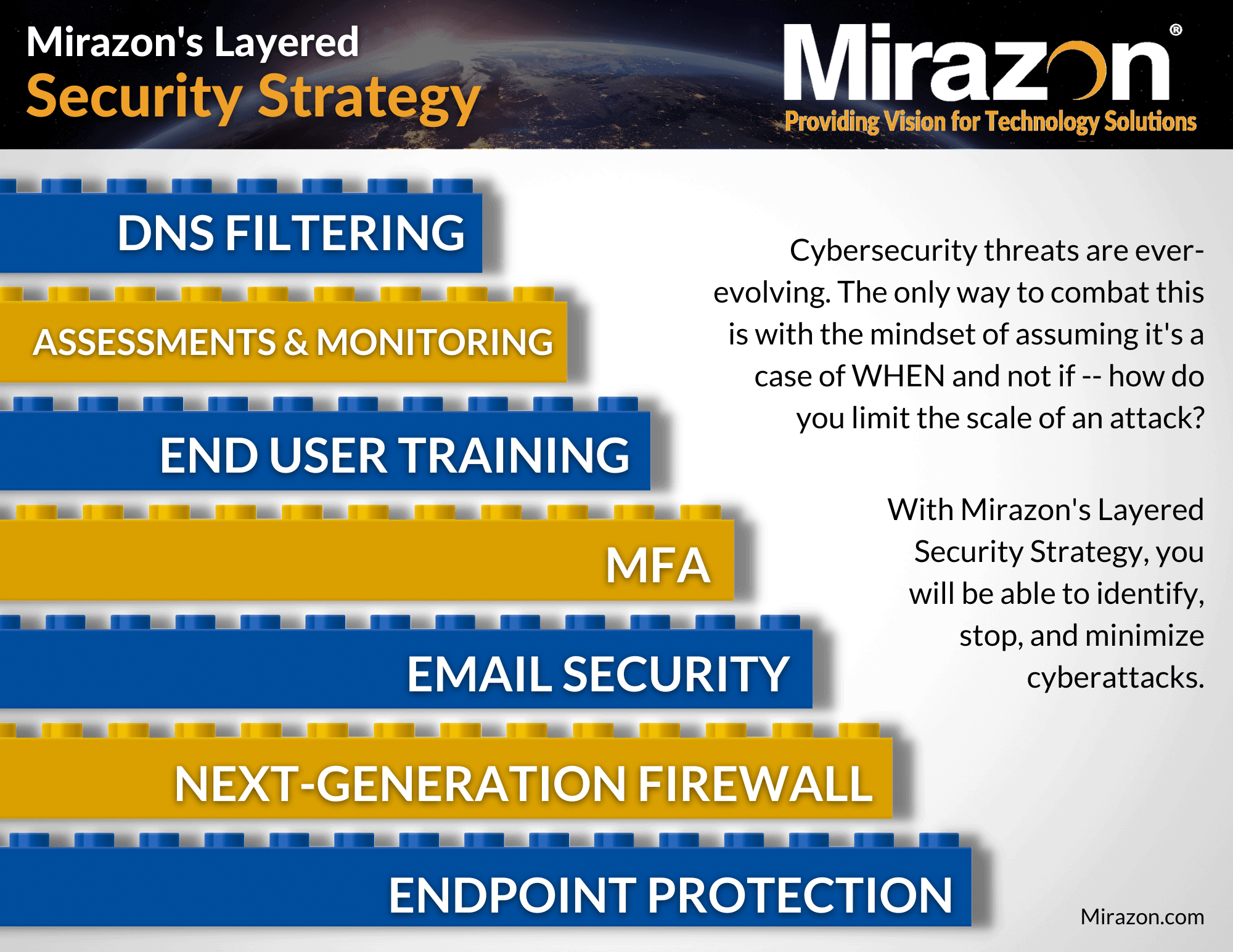
Well folks, we’ve finally made it to the last Defense In Depth blog and layer of our Layered Security Strategy: DNS Filtering.
As more people use the Internet and depend on it, the Domain Name System (DNS), which is like the address book of the Internet, has become even more important for how things work online. DNS Filtering is similar to a 24/7 professional monitoring service for your home. After all, you can’t be everywhere all of the time making sure your employees aren’t accessing harmful sites or clicking on malicious links. DNS filtering does that for you.
So, what exactly is DNS filtering, and how does it play a role in maintaining a robust Layered Security Strategy?
What Is DNS Filtering?
DNS acts as a directory service, translating human-readable domain names into machine-readable IP addresses, enabling seamless navigation between websites, applications, and cloud services that power modern businesses.
While cybersecurity threats continue to evolve in sophistication and scale, foundational components like DNS remain a vital, yet often overlooked, layer of protection. As the core nervous system for connectivity and information exchange, the DNS layer has emerged as a strategic point for enhancing security – but it is also an invaluable target for bad actors aiming to disrupt networks and steal sensitive data.
DNS Filtering Vs. Web Filtering
With DNS filtering, the firewall inspects DNS packets as they pass through, and it allows for malicious or undesirable web traffic to be blocked at the domain level rather than forcing you to inspect and take action on traffic at a more granular website-by-website level. It can be easier, more efficient, and more secure to block traffic to known-harmful domains in full using DNS filtering.
The firewall categorizes domains using machine learning and can take actions against entire categories with a simple configuration. For example, you can choose to block all domains within the “Spam” category but decide to monitor all domains within the “Social Media” category without needing to create more complex configurations on the firewall, such as deep packet inspection.
How Does DNS Filtering Work?
To start, let’s break down the three types of DNS filtering: blacklisting, whitelisting, and content filtering.
Backlisting
One of the primary functions of DNS filtering is to maintain a blacklist of known malicious domains. These are websites associated with phishing scams, malware distribution, or other cyber threats. When a user attempts to access a site, the DNS filter checks the requested domain against the blacklist. If it’s a match, access is denied, preventing potential security breaches.
Whitelisting
On the flip side, DNS filtering also employs whitelists, which contain trusted and approved domains. This ensures that users can only access pre-approved websites, reducing the risk of exposure to harmful content. Organizations often use whitelisting to control and limit internet access in workplaces or educational institutions.
Content Filtering
DNS filtering can also be used for content filtering, allowing administrators to control the type of content that users can access. This can include filtering out explicit or inappropriate material, enforcing compliance with regulatory requirements, or restricting access to specific categories of websites.
Now that we’ve covered the different types of DNS filtering, let’s talk about how it works in practice:
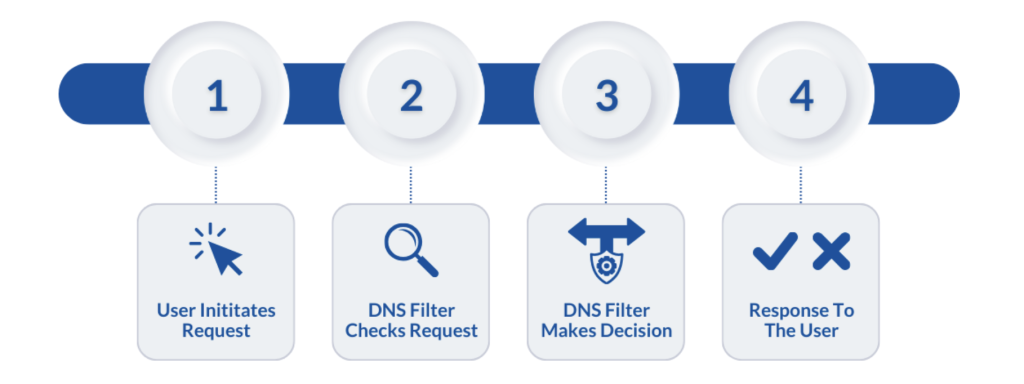
User Initiates Request
When a user enters a website URL into their browser, the computer sends a DNS resolution request to the configured DNS server.
DNS Filter Checks Request
The DNS filter intercepts the request and checks the domain against its database, which includes both blacklisted and whitelisted domains.
DNS Filter Makes Decision
Based on the filtering policies in place, the DNS filter makes a decision. If the domain is on the blacklist, access is denied. If it’s on the whitelist, access is granted. Content filtering policies also apply.
Response To The User
The DNS filter responds to the user’s request by either redirecting them to a block page for denied access or allowing the connection to proceed.
Of course, we could go into the technical details of DNS filtering all day (if you’re interested in the intricacies, please contact us!). However, in a general sense, the first step is when the user initiates the request to visit a website URL. Then the DNS filter will check and verify the request, checking the domain requested against both blacklisted and whitelisted domains, while also taking into consideration any content filtering policies that may apply. Once this is complete, the DNS filter will then decide if access should be granted to the requested website URL. Finally, the DNS filter will provide a response to the user, either giving them access to said URL or denying it.
Now that we know the basics of how DNS filtering works, let’s talk about why it’s so important to your IT system’s security.
Why Is DNS Filtering Important?
Enhanced Security
DNS filtering serves as an additional layer of security, blocking access to malicious websites and preventing cyber threats from infiltrating networks. Without proper security safeguards, DNS queries leave open opportunities for malicious actors to observe patterns, infiltrate systems, and potentially disrupt connectivity across your entire infrastructure. DNS filtering helps strengthen an organization’s security posture by filtering malicious domain requests through intelligent categorization and blocking.
Content Control
Content control through DNS filtering is vital for organizations, offering a streamlined approach to enforcing company policies, ensuring regulatory compliance, and mitigating various risks. By restricting access to non-work-related or potentially harmful websites, DNS filtering enhances productivity, protects against legal liabilities, and safeguards against cyber threats. This level of control is particularly beneficial in industries with strict regulatory frameworks, enabling organizations to customize content policies based on their specific needs and foster a secure online environment for employees.
Bandwidth Optimization
DNS filtering is a key player in boosting business network performance. It cleverly manages bandwidth by restricting access to non-essential or data-heavy websites. This ensures resources are used wisely, cutting down delays in the network. The focus on essential applications not only enhances security against potential threats but also proves valuable during emergencies, maintaining continuity without network slowdowns. In a nutshell, DNS filtering is the support system that keeps businesses running smoothly, giving priority to essential traffic for improved productivity and responsiveness.
Conclusion
In conclusion, DNS filtering is a powerful tool in the cybersecurity toolkit, providing a proactive defense against online threats and allowing organizations to maintain control over their digital landscapes. As the internet continues to evolve, understanding and implementing DNS filtering mechanisms, such as Webroot, become increasingly vital for a secure online experience and a strong layered security strategy.
Thanks for joining us on this Layered Security Strategy journey! You can find all of the Defense In Depth blogs at the bottom of this post, and as always, please reach out to us if you have any questions!
If you’d like to learn more about DNS filtering and how to implement it into your security strategy, please contact us by calling (502) 240-0404 or emailing info@mirazon.com.