Reach Out – We're Listening!
Have questions or need assistance? Drop us a line – we can’t wait to meet you.
Headquartered in Louisville, Kentucky, we proudly deliver world-class IT support and solutions to customers across the nation.
Having backups of your data is critical to protect against a myriad of threats, from ransomware or other bad actors to even power outages and equipment failures. Our rule is 3 backups on 2 different types of media with 1 being offsite, 1 being in the cloud, and test restores resulting in 0 errors.
Your backup and DR solutions should be as robust as you, but tailored just to your level of need. It’s easy to go overboard – just as easy as it is to overlook crucial areas that need protection. We can help you prioritize, document, and design the right solution for what you need.
Your backup and DR architecture could be the last line of defense standing between you and ransomware. With our skilled security and virtualization engineers, we can design a backup and DR environment the bad guys can’t touch – giving you the ability to restore quickly in the event of an attack.
We understand that creating a strategy for data protection is complex at best. That’s where we come in. Our experts will work with you to create a data protection strategy that works for you and your business while ensuring you have everything you need, and nothing you don’t.
Review the security health of your backups and create a plan for improvements
Our security assessments are a great tool to review the critical elements of your environment and identify areas of vulnerability. We offer several packages, and backup security is just one of them.

Lightweight agents on your production, backup, and DR systems that stop attacks and notify you quickly.
Endpoint detection and response (EDR) tools can come paired with 24/7 threat hunting, but at minimum have intelligence to watch for suspicious behavior on your endpoints and in your network. Deploying this helps you on the frontlines in protecting your data.

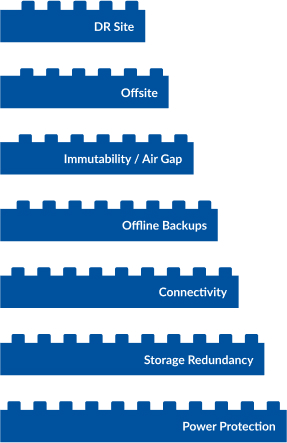
A great backup and DR architecture plan stands between you and critical data loss.
A DR and backup plan is a frequently overlooked piece of your data protection strategy, and frequently organizations scramble to assemble something simply to satisfy a compliance or vendor requirement. However, this could be your Deus Ex Machina in the event of a ransomware attack, not to mention a variety of other environmental threats to your systems.

Protecting your data is easier said than done. That’s why we use our proven processes and layered strategies that will not only meet your needs for today, but will also prepare your infrastructure for the future.
Our experienced team can help you design your systems and policies around the latest threats and hacker methods to limit your attack surface.
The best mindset when it comes to your cybersecurity strategy is to assume it’s a matter of WHEN and not IF. Then write your plans and documentation accordingly.
What good are backups if they don’t work? What good is a plan if you never tried it? Allow us to guide you through testing the elements of your data protection strategy both separately and together so we stay prepared.
Navigating the vagaries of insurance forms can be frustrating. Let’s pick apart the requirements and plan for any remediation or assessments needed.
When it comes to cybersecurity, the conversation should start with data protection. This is your backstop in the event of a fire, theft, encryption, or other form of disaster.
With Mirazon’s Layered Data Protection Strategy, you will be able to protect your data, and business, on every level.