
64 fixes have been provided by Microsoft to address security weaknesses in all of its products, including 11 critical flaws – six of which are currently being actively exploited by hackers.
Here is information about those six.
Exchange Vulnerabilities
CVE-2022-41040 and CVE-2022-41082 are two security flaws in Microsoft Exchange Server that have been actively attacked since September. These are addressed by two of the critical upgrades.
Security Updates (SUs) have been made available by Microsoft for vulnerabilities discovered in:
- Exchange Server 2013
- Exchange Server 2016
- Exchange Server 2019
Both the original update packages (.msp files) and self-extracting auto-elevating.exe packages for SUs are available from the Microsoft Update Catalog.
The following specific Exchange Server versions can use the November 2022 SUs:
- Exchange Server 2013 CU23 (support ends in April 2023)
- Exchange Server 2016 CU22 and CU23
- Exchange Server 2019 CU11 and CU12
Because we are aware of operating exploits of related vulnerabilities, we recommend that you install these updates immediately to protect yourself from these attacks.
The zero-day vulnerabilities published publicly on September 29, 2022 are fixed in the November 2022 SUs (CVE-2022-41040 and CVE-2022-41082).
Customers of Exchange Online are already shielded from the security holes fixed in these SUs, therefore all that is required of them is to update any Exchange servers that are present in their environment.
The Security Update Guide has more details about particular CVEs (filter – Exchange Server under Product Family).
Microsoft has released the following updates below:
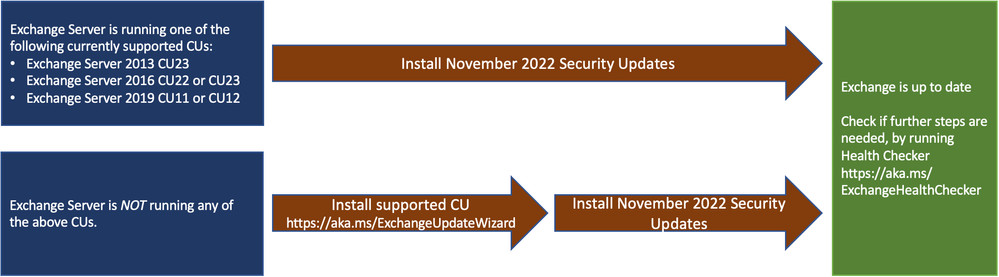
- Install the latest CU. Go to Exchange Update Wizard and choose your currently running CU and your target CU to get directions.
- Inventory your Exchange Servers to determine which updates are needed using the latest release of the Exchange Server Health Checker script. Running this script will tell you if any of your Exchange Servers are behind on updates (CUs, SUs, or manual actions). Re-run Health Checker after you install the SU to validate no further action is needed.
- If you encounter errors during or after installation of Exchange Server, run the SetupAssist script. If something does not work properly after updates, see Repair failed installations of Exchange Cumulative and Security updates.
You can find FAQs for these vulnerabilities here.
Windows Vulnerabilities
A third zero-day, CVE-2022-41128, is a serious Windows flaw that enables remote code execution by threat actors. For this vulnerability to emerge, a user running a vulnerable version of Windows must connect to a rogue server. An attacker would need to host a website or server share that has been specially built, and users cannot be forced to visit by an attacker; instead, users must be persuaded to do so, usually by means of an alluring email or message.
Two more Windows vulnerabilities include CVE-2022-41125 and CVE-2022-41073. While CVE-2022-41125 exists in the Windows CNG Key Isolation Service, CVE-2022-41073 impacts the Microsoft print spooler. Both of these vulnerabilities could allow an attacker to gain SYSTEM privileges.
This month’s final zero-day patch is also in Windows. CVE-2022-41091 lets hackers build malicious files that are designed to interact with security mechanisms that rely on Mark of the Web (MOTW) tagging, such as Protected View, in Microsoft Office.
A specially crafted.url file that is intended to exploit the bypass could be sent to the targeted person in an instant message or email attack scenario. Websites that have been compromised or websites that allow or host user-provided material might have specifically prepared content that takes advantage of this security feature bypass.
In all circumstances, an attacker would not be able to force a victim to view maliciously controlled material. Instead, a potential attacker would need to persuade a user to act. They might, for instance, persuade a user to send an infected file or click a link that takes them to the attacker’s website.
This month’s Patch Tuesday resolved 68 vulnerabilities in total. Microsoft rated 11 of them as “critical” and the remaining ones as “important” in terms of severity. Patches are typically installed automatically within 24 hours or less. Go to Windows > Settings > Updates and Security > Windows Update if you want to install updates right away. Here is Microsoft’s whole breakdown.
In order to protect your business, employees, and IT infrastructure you must take a proactive approach. Through the use of Layered Security Strategy, our experts can ensure that your assets are properly protected and secure. Reach out to us if you’d like to learn more by using the information below!