How I Learned to Automate Almost Everything on a Windows System
You’re about to rest on your laurels after a successful remote access VPN implementation. Your firewall (maybe it’s a FortiGate) is humming along. End users are connecting. They’ve got access across the network. File shares work. Printing works. It is a glorious, glorious day.
Then you hear that familiar notification sound of a new email…with the subject something along the lines of, “Remote users not getting login scripts” or “Remote users not getting group policy.” Crap.
So you fire up your VPN client, edit settings, aaaand…
It’s pretty bare bones.
Not to fear. You fire up your FortiGate and edit the VPN settings, aaaand…
Again. Not what we’re looking for. How about the VPN portal settings?
Strike three!
Before you reply, “Sorry, can’t be done,” there is a solution to this problem.
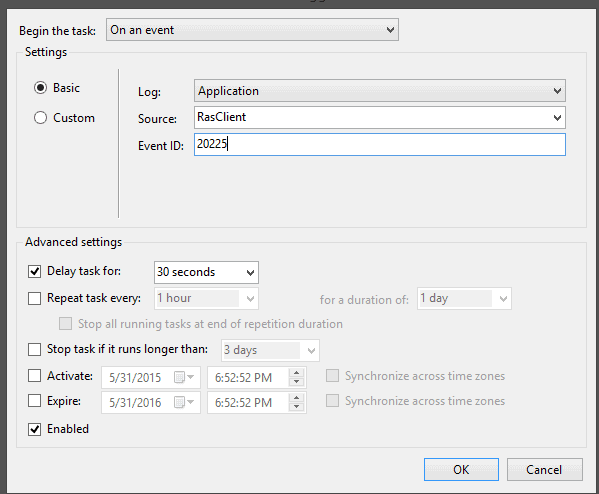
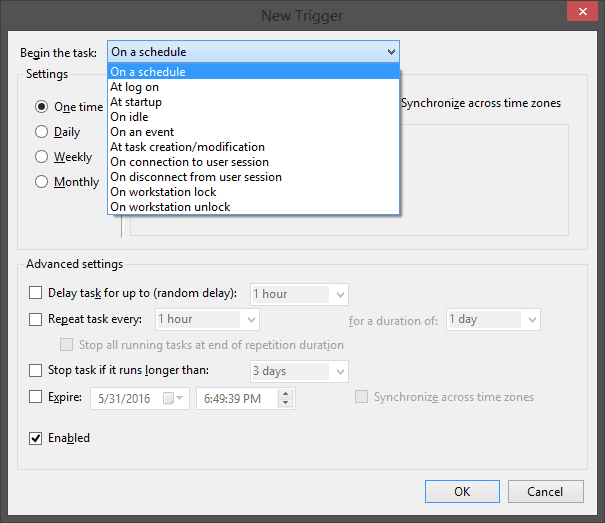
Something cool that came out of Windows Vista — words you thought you’d never hear — was an expanded and updated Task Scheduler. The new Task Scheduler allows you to “schedule” a task with a whole series of triggers. Perhaps the most useful of these is “on an event.”

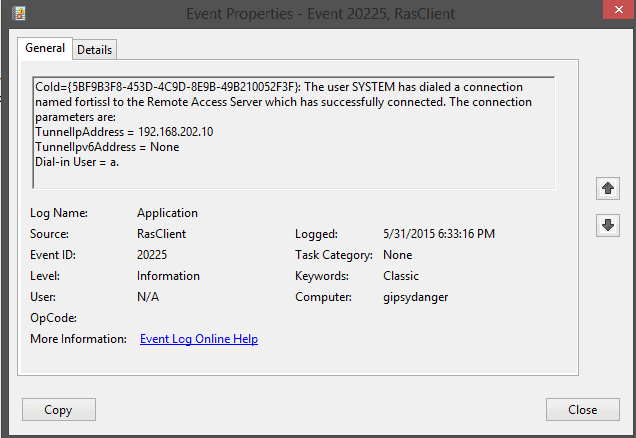
That’s right! You can set up Windows Task Scheduler to run a scheduled task when an event is logged in the event logs. In my case, I checked for “RasClient” Event ID 20225.
What does that event say?
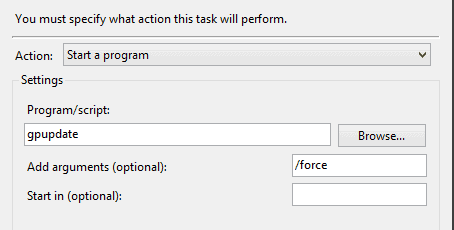
In a nutshell, I set a task to run 30 seconds after my VPN client is successfully connected. Side note: I chose a 30-second delay to make sure there was enough time for my computer to get its IP and DNS Settings and so on. In my case I tell the task to run “gupdate /force.”
But, you are not limited to that. Do you want to run a script? Sure. Do you want to make sure the client computers all register with DNS? You can do that too. Also, you are NOT limited to just VPN connection events. You can use task scheduler to trigger an action on ANYTHING that generates a log entry on any of the event logs.
Do you want to know the best part? This entire scheduled task can be pushed out via GPO.
The takeaway here is that what started as a quest to solve a simple problem (VPN users not getting group policy updates), ended up with a way to automate almost limitless things on your end users’ systems.
Or, you can use Event: Source = Outlook, Event ID = 32 to trigger this WAV on a colleague’s computer.
Remember, with great power comes great responsibility!