According to recent research, Microsoft’s desktop operating system has a major ransomware vulnerability. It’s nearly invisible, encrypts files using a completely legal protocol, and comes pre-installed on all new Windows systems: OneDrive. Despite its solidified reputation, there’s now a OneDrive vulnerability that can turn this useful tool into a ransomware double agent.
The conclusive observations derived from the research led by Or Yair, a cybersecurity analyst with SafeBreach, were showcased at the Black Hat event. His findings show the keen readiness of OneDrive to function as a harmful collaborator by being manipulated against its original purpose of providing safe cloud storage synchronicity.
The series of oversights by Microsoft and its associated third-party vendors illustrated OneDrive’s susceptibility to manipulation, easily deceived into encrypting any accessible files it can get its hands on. This raises an intriguing question: “How did Yair manage to transform a presumably incredibly secured feature into a dangerous threat against the very systems it was designed to safeguard?”
How Can OneDrive Become A Ransomware Double Agent?
The initial step to turn OneDrive into a ransomware double agent involved stealing someone’s account, a task that Yair found surprisingly easy once he had successfully infiltrated a Windows PC.
What Yair discovered was that OneDrive stores its log files in a specific directory linked to the logged-in user. Within these logs were session tokens that Yair claimed to extract after obtaining a copy and parsing the log file. These stolen tokens provided the starting point for Yair’s actions.
Moving beyond OneDrive’s designated directories was straightforward. Yair explained that although symbolic links could only be created by an administrator (which he wasn’t during the experiment), junctions, albeit restricted to pointing to a directory rather than an individual file, could be generated by anyone. Leveraging this, Yair created junctions to locations beyond OneDrive’s directory, granting the ability to create, modify, or delete files on the local machine.
OneDrive has safeguards that ensure there are shadow copies of files that can be recovered in the event of an attack, preventing ransomware from erasing backups. However, Yair found a loophole in the OneDrive app for Android, which used a distinct API compared to other OneDrive apps. Exploiting this difference, Yair was able to erase the original copies of encrypted files in a manner that rendered them irretrievable, leaving the victim only with encrypted backups of the encrypted files.
EDR Won’t Save You Here…
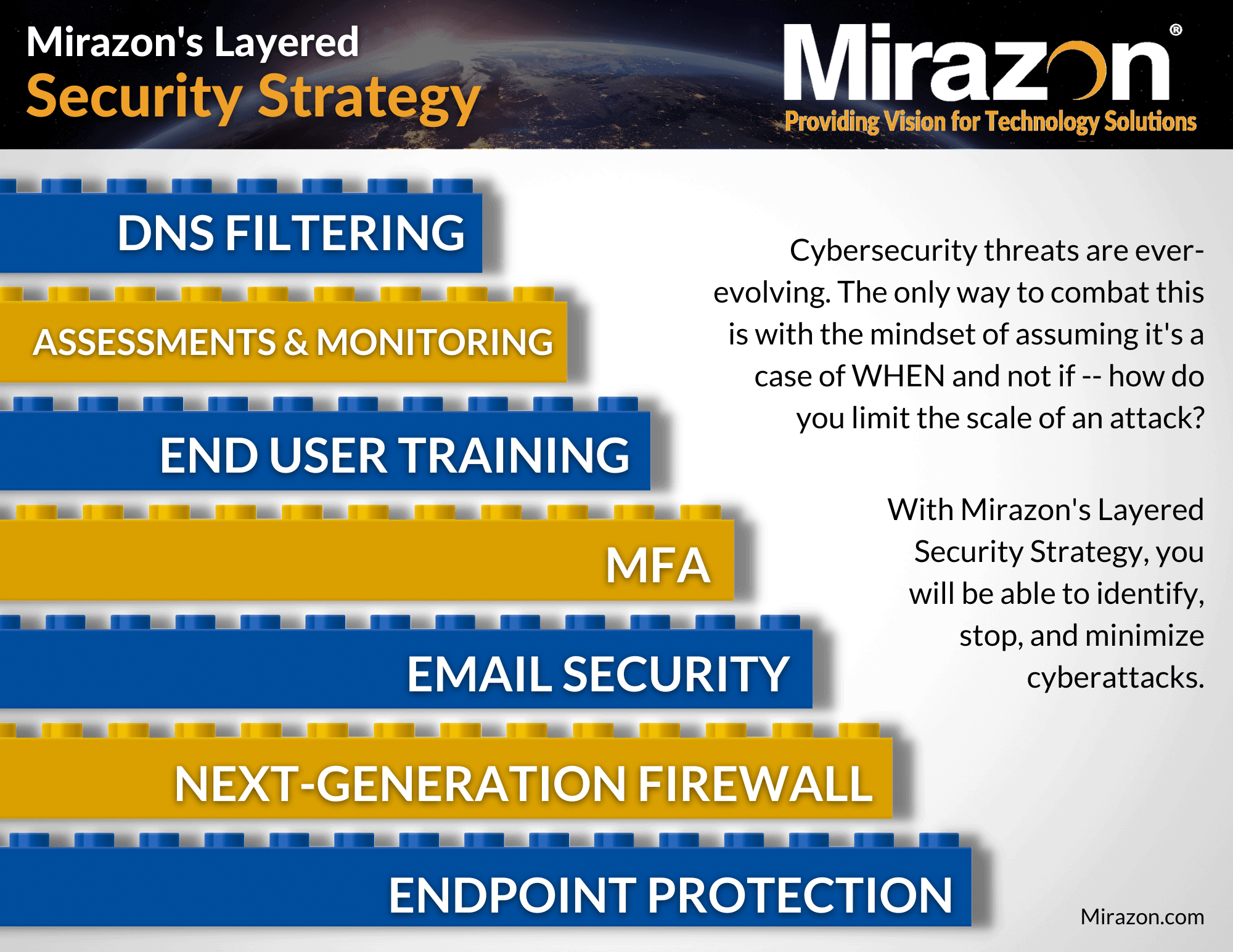
When facing a ransomware threat where a seemingly legitimate program unexpectedly starts encrypting data on a device, the instinct is to rely on EDR software for protection. Afterall, it is the very first layer of our Layered Security Strategy.
Well… About that…
Despite being from major corporate manufacturers, several software solutions failed to detect the spy-like behavior within OneDrive. According to Yair, EDR software should ideally detect activities like deletion of shadow copies, but in this case, CyberReason, Microsoft Defender for Endpoint, CrowdStrike Falcon, and Palo Alto Cortex XDR all fell short in identifying this malicious activity.
On a positive note, SentinelOne’s software successfully detected and warned about the potential ransomware attack – but it still couldn’t prevent the destruction of shadow copies due to the fact that OneDrive’s local executable is on the allow list.
OneDrive employs well-known and trusted file extensions for encrypted files, operates in otherwise restricted directories, and doesn’t trigger alarms when modifying decoy files due to its established trust in many EDRs. Importantly, there’s no actual malware present on the target computer, making it difficult to identify with static signatures.
Consequently, if a hacker gains control over a Windows desktop, they can potentially utilize a trustworthy piece of software to encrypt a significant portion of the system. Given these circumstances, a pertinent question emerges: “Is there an effective approach to countering such attacks?”
Preventing OneDrive From Becoming A Ransomware Double Agent
Following the revelation by Yair, reports indicate that Microsoft has taken steps to fix the issue. Additionally, Crowdstrike, CyberReason, and Palo Alto have also made necessary updates to their EDRs to address the problem.
In a broader context, applications need to determine when to stop automatically trusting processes, even if they originate from a reputable source like Microsoft. Yair emphasized the need for security vendors to assess the possibility of attackers gaining control over critical processes such as OneDrive.
Detecting and preventing such unauthorized control is crucial to ensuring robust security measures. To put it simply, it’s about understanding potential risks and taking action to stop them before any harm occurs. Take a look at our Microsoft Solutions.
If you want to know more about how to prevent OneDrive from being used as a ransomware double agent, please contact us by calling (502) 240-0404 or emailing info@mirazon.com.