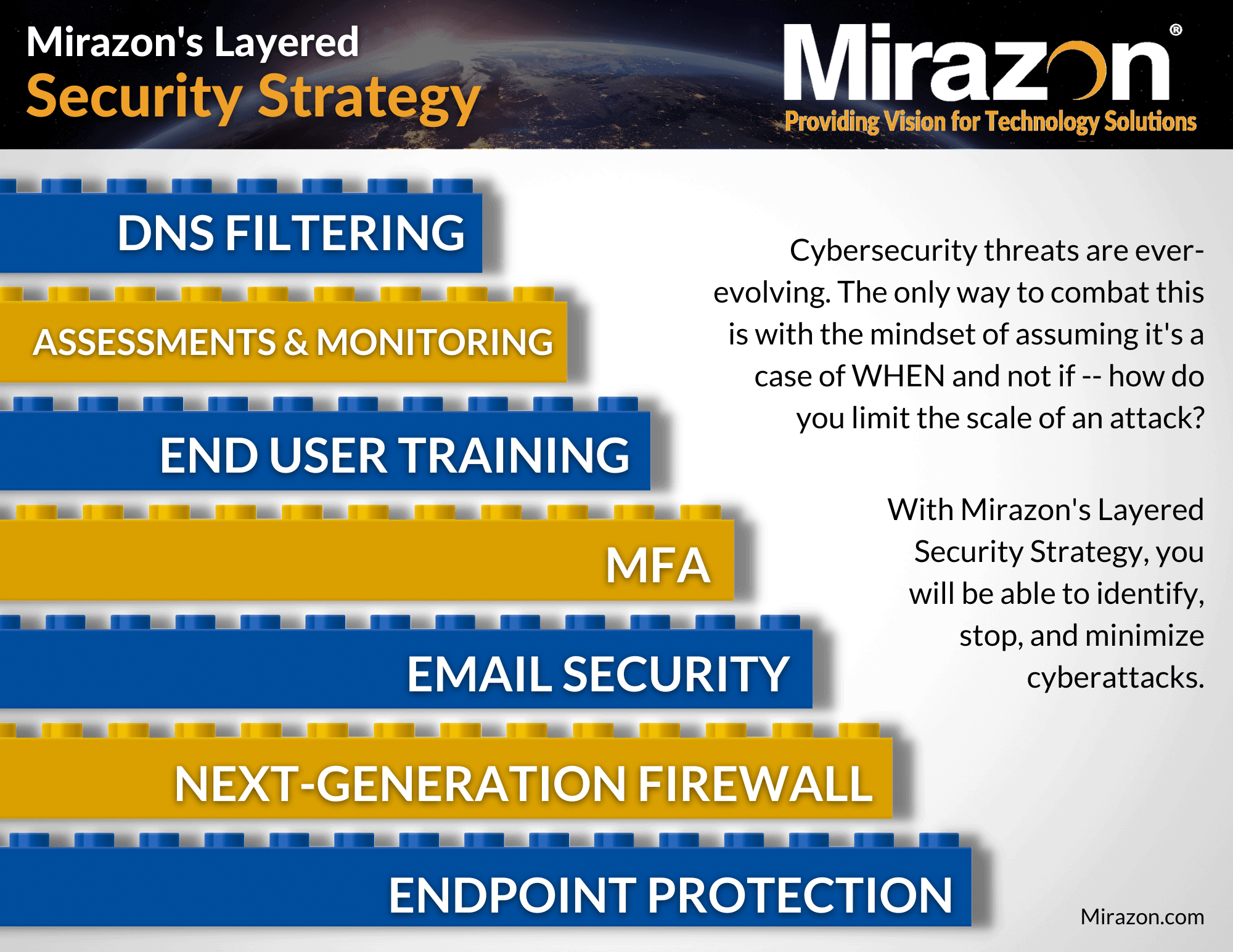
In today’s digital age, the security of your endpoints (i.e., laptops, tablets, smartphones, etc.) has become more critical than ever. With the rise of remote work and BYOD policies, the attack surface for cybercriminals has expanded, increasing the need for endpoint protection. The consequences of a breach can be catastrophic, ranging from data loss and financial damage to a tarnished reputation. In this blog, we’ll discuss why endpoint protection is essential to cybersecurity and how you can implement it effectively.
Endpoint Protection Vs. Antivirus Software
Endpoint protection goes beyond antivirus and focuses on the overall security of your endpoints. While antivirus software, such as McAfee or Norton, may detect and remove known malware, endpoint protection provides comprehensive protection against a wide range of threats, including zero-day exploits, advanced persistent threats, and insider threats. Endpoint protection typically includes features such as firewalls, intrusion detection and prevention, data encryption, and access control. It is vital to the overall health of your business and IT infrastructure, which is exactly why it’s the foundation of our Layered Security Strategy.
Download Our Layered Security Strategy Guide
Endpoint Protection Strategies
Effective endpoint protection requires a multi-layered approach (similar to the above image). It starts with identifying your endpoints, including devices running on your network and those brought in by employees. Once you’ve identified your endpoints, you can then create policies for managing them, such as patching and updating software, disabling unused ports and services, and enforcing password policies. Additionally, you can implement security tools such as MDM, SIEM, and EDR to monitor, detect, and respond to threats effectively.
Risks To Endpoints
Endpoints are the most vulnerable points in any network, making them a prime target for attackers. Cybercriminals often use social engineering tactics to trick users into revealing sensitive information or downloading malware. Additionally, endpoints are often the entry point for attacks, such as ransomware or DDoS attacks. Protecting your endpoints requires being aware of these risks and taking proactive measures to prevent them from ever happening in the first place.
Compliance Requirements
Endpoint protection is not only critical for cybersecurity, but it’s also essential for compliance with regulations such as HIPAA, PCI, and GDPR. These regulations require organizations to implement measures that protect the confidentiality, integrity, and availability of sensitive data. Implementing endpoint protection can help you achieve compliance by ensuring that your endpoints are secure, and that any data stored or transmitted on them is protected.
Importance Of Employee Education
Even with the best endpoint protection in place, employees can still be a weak link in your security chain. Employees may inadvertently download malware, fall for phishing scams, or use weak passwords – all of which can lead to a breach. Educating employees using our Security Awareness Training on cybersecurity best practices, such as how to identify and avoid phishing emails and the importance of strong passwords, can go a long way in preventing attacks.
Endpoint protection is an essential part of any cybersecurity strategy. By implementing a multi-layered approach that includes identifying endpoints, implementing policies, and using security tools, you can protect your organization from a wide range of threats. Additionally, being aware of the risks associated with endpoints, complying with regulations, and educating employees can help you stay ahead of the curve and keep your endpoints secure. Don’t wait until it’s too late – start protecting your endpoints today using our proven processes that we’ve mastered over decades of experience.
In our next Defense In Depth blog, we’ll be talking about the second layer in our Layered Security Strategy: Next-Generation Firewalls (NGFWs).
If you’d like to learn more about endpoint protection and security, please contact us by calling (502) 240-0404 or emailing info@mirazon.com.