
Since the outbreak of the COVID-19 pandemic, thousands of restaurants and businesses have replaced tangible menus and guides with QR codes that link to webpages carrying the same information. While some individuals come up with inventive methods to use QR codes to make our everyday lives easier, others think of sneaky ways to take advantage of them.
So, let’s shine a light on the dark side of QR codes, shall we?
The Dark Side Of QR Codes
Hackers have jumped on the opportunity and started spreading fake QR codes in order to steal customer data, and various forms of cybercriminals are attempting to take advantage of these QR codes – but why, you may ask?
Well… QR codes have a lower probability of being detected by cybersecurity defenses compared to URLs or attachments, making it easier for attackers to breach protective protocols and steal information. So, how does it work?
When you use your phone to scan a QR code, the phone’s built-in QR reader recognizes the code and takes you to the URL of the corresponding website, PDF file, picture, video etc. Without all the extra processes, it would be similar to putting a URL into a browser or clicking a link. There is no active tracking or data collection associated with the QR code itself, and the fundamental technology is relatively safe – but that doesn’t stop hackers from using it in phishing scams and other ways.
Cybersecurity Risks Of QR Codes
QR code security issues can be divided into two categories: counterfeit QR codes and QR code hijacking.
Counterfeit QR codes
Since QR codes instantly open links, hackers develop ways to substitute legitimate QR codes with counterfeit ones that direct users to different websites. This enables hackers to obtain personal information.
Cybercriminals can physically swap out one QR code for another in public areas (Texas police discovered malicious QR codes that covered legitimate QR codes on parking meters), or send emails that include fraudulent messages such as, “Your credit card information is out of date. Scan the QR code to continue renewing your autopay.”
A good example of this is using QR codes to expedite payments, which is incredibly convenient for the general population, but it’s also convenient for attackers – who have discovered ways to transfer those payments into their own accounts (as long as the fraudulent QR code was used, directing the user to a malicious site). As QR codes are increasingly being used in innovative ways to simplify processes, hackers themselves are coming up with innovative ways to take advantage of this vulnerability.
QR Code Hijacking
QRLjacking is an online attack that involves duping an unaware user into scanning the attacker’s QRL rather than the genuine QRL delivered by the service provider. When a user scans a malicious QRL, the attacker gains privileges to the user’s account – beginning their streak of havoc.
Like many online attacks, QRLjacking involves some type of social engineering to trick the target into scanning the compromised QRL.. Criminals look for websites that need a QR code to login in order to engage in a practice known as QRLjacking. QRLjacking occurs when someone uses a QR code as a one-time password, and an attacker clones the QR code and redirects the user to a phishing site.
Hackers utilize vulnerabilities to direct people in the wrong direction and gather data. When businesses and organizations fail to follow QR code best practices, such as creating a new QR code each time a user logs in, malicious actors can use this security vulnerability to redirect victims to a phishing site instead.
Which industries are vulnerable to this type of phishing attack?
One significant U.S. energy firm was the first target of the phishing attack, which then extensively targeted the manufacturing, insurance, technology, financial services, and healthcare sectors.
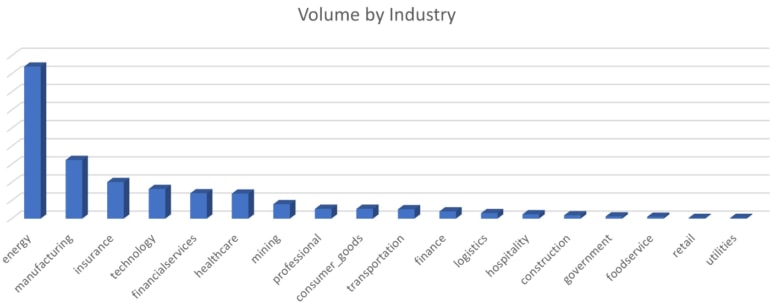
An analyst claims that from the campaign’s start in May 2023, the average month-to-month growth percentage exceeded 270% – and more than 2,400% more QR codes have been included in emails since May 2023.
But there is some good news….
Researchers have stated, “although QR codes are advantageous for getting malicious emails into user’s inbox, they may fall short of being efficient in getting the user to the phish.”
QR codes require a scanning device, which is typically a mobile phone because those devices frequently come equipped with a QR code scanner that functions with their camera. Additionally, these mobile phone scanners often display the link that the QR code contains to the user, who chooses whether or not to click on it. This is where Cybersecurity Awareness Training is key in protecting the business as a whole.
How To Minimize Security Risks From QR Codes
You can continue to utilize QR codes while protecting your personal information by using a reliable QR code generator when creating a QR code. If you don’t completely trust the source, avoid giving out personal information on websites that are launched with QR code shortcuts. Verify the QR code for any suspicious characteristics, such as typos or the incorrect logo.
Additionally, there is no need to add a separate QR code scanning program to your phone because it already has that capability. Lastly, double-check the URL. The URL to the website you’re about to visit will populate when you scan a QR code. Make sure it appears trustworthy and safe before clicking on it.
Always use a reliable antivirus program and family safety applications to identify malware as your first line of protection against viruses and phishing scams. Lastly, the FBI advises, “If scanning a physical QR code, ensure the code has not been tampered with, such as with a sticker placed on top of the original code. Do not download an app from a QR code. Use your phone’s app store for a safer download.”
Now that you know a little bit more about how QR codes operate, you can take advantage of their ease and lower any security threats.
Examples
Heinz Ketchup had a promotion in 2015 where customers could design their own ketchup bottles by scanning a QR code that directed them to a specific website where customers could make their designs and purchases. Heinz failed to renew the domain for that website, and a hacker took full advantage – purchasing the domain and diverting visitors to a malicious website instead, collecting their personal information along the way.
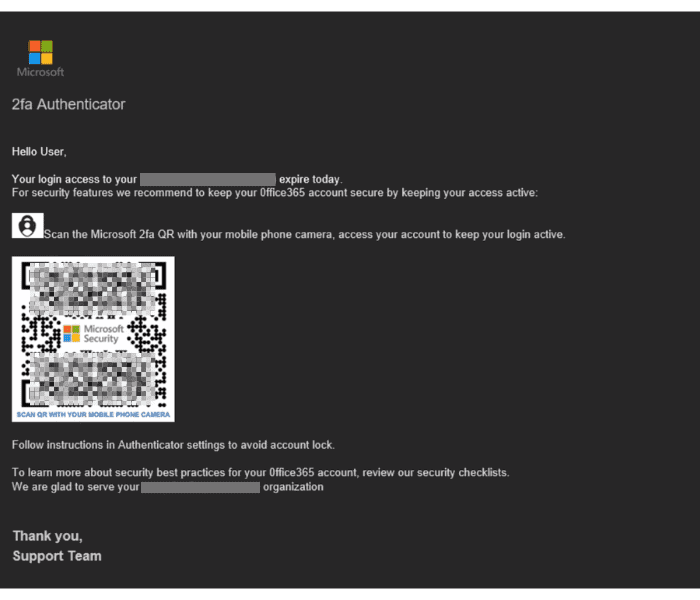
More recently, there have been several malicious QR phishing campaigns – and attackers are claiming to be from Microsoft Authenticator. In this effort, QR codes are used as PNG pictures that, when scanned, open phishing websites for Microsoft credentials. The email content employs various – but similar – enticements, such as convincing the user that they must upgrade their account security or enable two-factor authentication/multi-factor authentication within 72 hours. If an end-user mistakenly trusts the source, all it takes is for them to enter their credentials and attackers will possess their login information and personal data. Here is a screenshot of what this phishing campaign can look like (don’t worry – I blurred the QR code image):
In today’s environment, you can never be too careful – so make sure you THINK before you SCAN. Also, make sure to check out our other cybersecurity services and how you can implement a Layered Security Strategy in your business’s environment – protecting your employees and IT infrastructure from all sides.
If you’d like to learn more about this cybersecurity risk related to QR codes, or how you can better protect your business, employees, and IT infrastructure from this risk, please contact us by calling (502) 240-0404 or emailing us at info@mirazon.com.