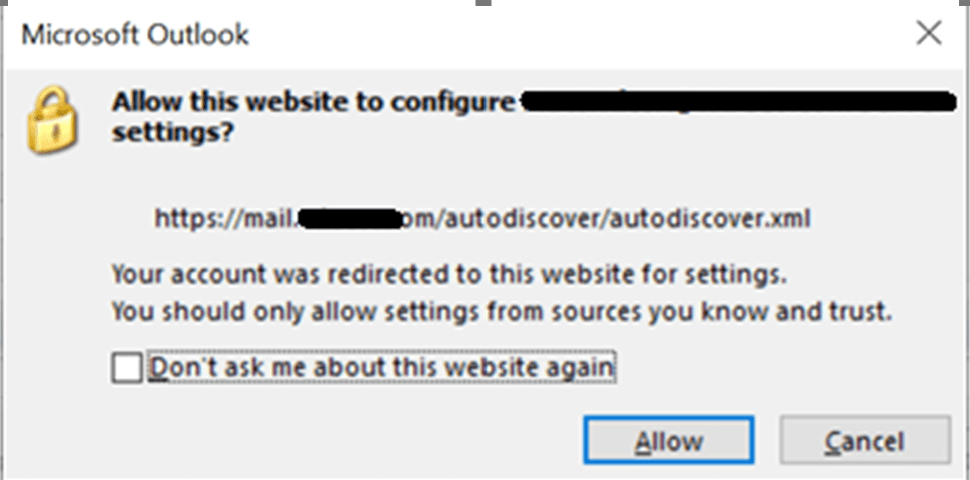
UPDATE 9/30/2022: We have found in one on-prem only environment running Exchange 2019, the Outlook users got prompted with the typical “Allow this website to configure…” popup, then they got prompted to log in. When they enter their credentials, their login fails to Microsoft. They do not have Microsoft 365. We are currently investigating the cause of this. Until we find the solution, we had to revert the changes.
Microsoft released a notice yesterday detailing information about vulnerabilities CVE-2022-41040 and CVE-2022-41082 in Exchange Server 2013, 2016 and 2019. There are two vulnerabilities in question: CVE-2022-41040, a Server-Side Request Forgery (SSRF) vulnerability, and CVE-2022-41082, which allows remote code execution (RCE) when PowerShell is accessible to the attacker.
Although authenticated access to the vulnerable Exchange server is necessary to successfully exploit these vulnerabilities, it’s still important to take action as quickly as possible.
According to Microsoft’s post:
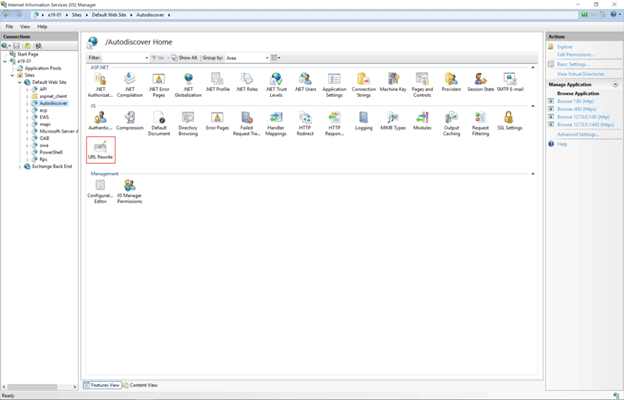
The current mitigation is to add a blocking rule in “IIS Manager -> Default Web Site -> Autodiscover -> URL Rewrite -> Actions” to block the known attack patterns.
Microsoft has confirmed that the following URL Rewrite Instructions, which are currently being discussed publicly, are successful in breaking current attack chains.
Step by step instructions follow below on the Microsoft notice but please note we made some corrections.
The following URL Rewrite Instructions, which are currently being discussed publicly, are successful in breaking current attack chains.
- Open the IIS Manager.
- Expand the Default Web Site.
- Select Autodiscover.
- In the Feature View, click URL Rewrite.
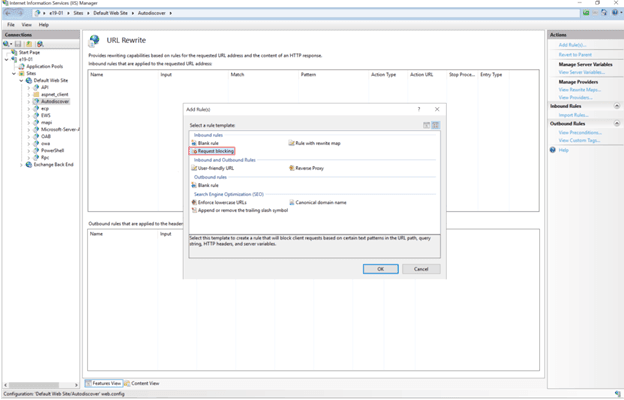
- In the Actions pane on the right-hand side, click Add Rules.
- Select Request Blocking and click OK.
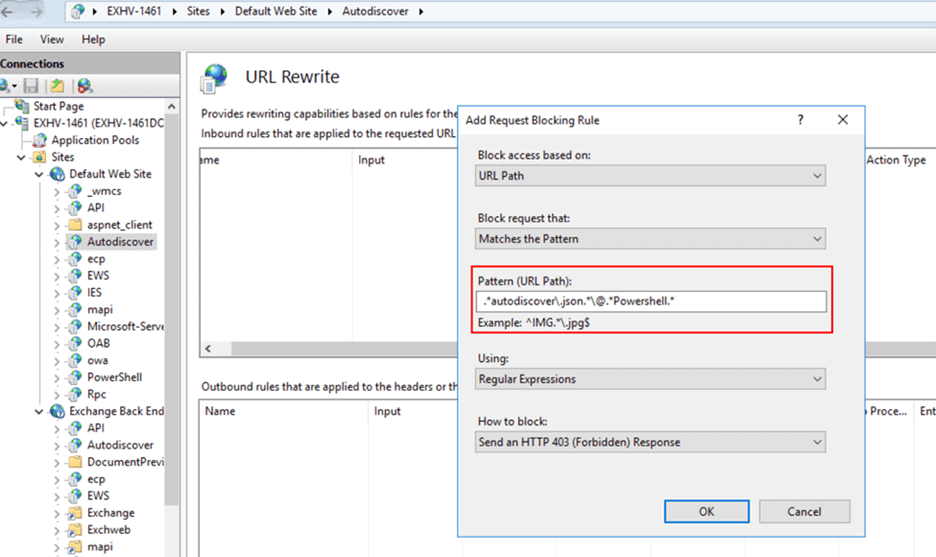
- Add String “.*autodiscover\.json.*\@.*Powershell.*” (excluding quotes)
- Change the Using drop-down to “Regular Expressions”
- Click OK.
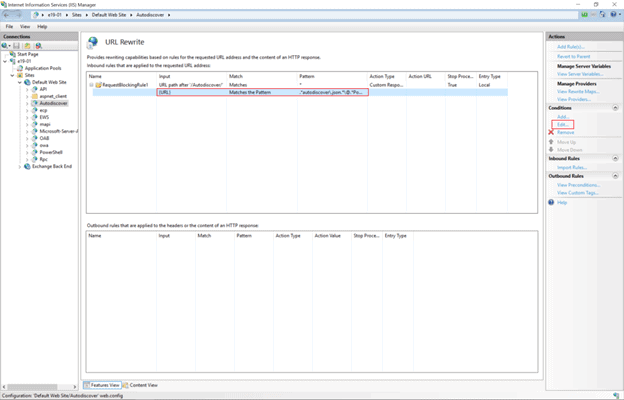
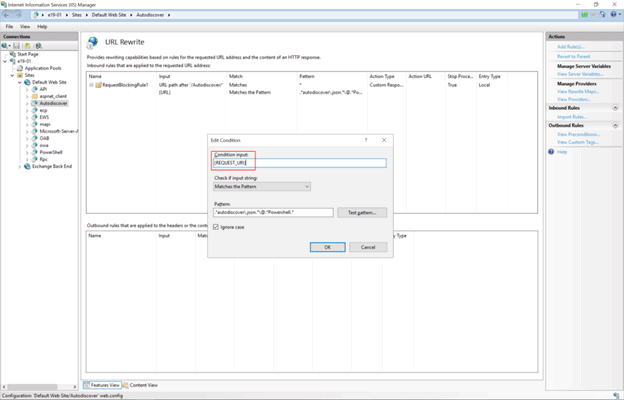
- Expand the rule and select the rule with the Pattern “.*autodiscover\.json.*\@.*Powershell.*” and click Edit under Conditions.
- Change the condition input from {URL} to {REQUEST_URI}
Impact: There is no known impact to Exchange functionality if the URL Rewrite module is installed as recommended.
Authenticated attackers who can access PowerShell Remoting on vulnerable Exchange systems will be able to trigger RCE using CVE-2022-41082. Blocking the ports used for Remote PowerShell can limit these attacks.
- HTTP: 5985
- HTTPS: 5986