
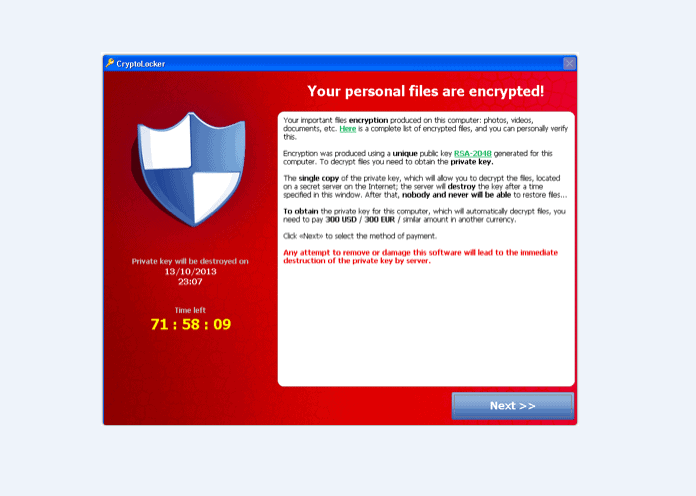
 Cryptolocker ransomware is making its rounds. This virus basically infects your computer or network, encrypts all of the data, and holds it hostage until someone pays a ransom. If a victim pays the ransom, he may be provided with the key to unencrypt the data…and maybe not. There are many versions of this virus in the wild.
Cryptolocker ransomware is making its rounds. This virus basically infects your computer or network, encrypts all of the data, and holds it hostage until someone pays a ransom. If a victim pays the ransom, he may be provided with the key to unencrypt the data…and maybe not. There are many versions of this virus in the wild.
The latest version is aggressive and uses very sophisticated encryption. Currently there is no way to unlock these files without paying for the key. If you do not have the key, the files could be gone forever.
Why it’s trouble
The scary part about this virus is how stealthy it is. The virus starts encrypting files in the background, this may take days to complete. You will not even know you have a problem until it is too late. Currently anti-malware software is not effective in detecting this virus. Once you get the notification from the virus, your files are already encrypted.
The only way to get your data back is to restore it from backup. Here’s the rub: since the virus takes several days to work, nightly backups are usually useless.
If Cryptolocker infects your network…
This virus is usually launched from an unauthorized attachment. Most of the time the virus will prompt you to purchase the unlock key. Don’t do it!
In a vast majority of cases, you never get the key, or if you do get the key, you are funding the very problem you are trying to avoid. If you get infected by this virus, your best bet is to restore from backup. But, as I mentioned before, backups from at least three days before are usually useless.
How to prevent Cryptolocker
Advise staff to not open unfamiliar files, and do not go to unfamiliar websites. If at all possible, do not allow staff to log on to their computers as administrator. Non-IT personnel should always have “user” access to computers for daily activities.
Using a backup strategy to mitigate loss
Having a good backup strategy is the key to fighting a virus like CryptoLocker. We all know we should do daily backups, and a good percentage of people do.
However, as mentioned before, a daily backup will not help in this situation. Most people do a backup on Monday, then overwrite or update the Monday backup on Tuesday, which means there’s only one copy. So, if you can follow along here: if I have a good backup on Monday, get hit by the virus on Tuesday, but don’t know I am infected until Friday then every nightly backup since Tuesday will be infected!
If you don’t have the full backup from Monday because it updated on Tuesday, then you are in trouble. We always stress keeping as many backups as you can. In this case, having two weeks’ worth of backups, would ensure complete data recovery in case of virus attack.
With our backup and disaster recovery solutions, we try to store three different versions on at least two different mediums, with one being offsite.